
In most forms of corruption, the easiest targets are not senior decision-makers but the lowest-paid employees who quietly keep operations running. The same pattern holds true in cybersecurity. Routine, low-visibility roles such as outsourced support technicians, help-desk operators, or vendor engineers with privileged access can become the simplest, cheapest and most effective entry points into an organization.
In 2025, we saw at least one major data breach tied to a bribery case. The issue has been on my mind all year, even before the Coinbase hack, and it was reinforced by the recent Discord incident reportedly involving a remote employee who accepted a bribe. In contrast, Tesla’s attempted breach shows a very different outcome, and comparing the three cases offers potential insight into the conditions that make bribery possible.
Coinbase Leak

Between late 2024 and early 2025, overseas employees of TaskUs, an outsourcing partner of Coinbase, reportedly took thousands of photographs containing clients’ personal data, including names, addresses, and bank details. This information was later shared with a third party and likely used to support social engineering attacks.
Reportedly, the India-based TaskUs employees were paid around $200 per photograph, with total payouts estimated to exceed $500,000.
Based on data from platforms such as Glassdoor and Indeed, the monthly salary of a service desk technician in India typically ranges between $400 and $1,000. This means that taking just two to five photographs of Coinbase customer data at $200 per image would be enough to match a full month’s pay.
In a blog published on May 15, 2025, titled ‘Protecting Our Customers – Standing Up to Extortionists’, the Coinbase team explained the scale and cause of the attack:
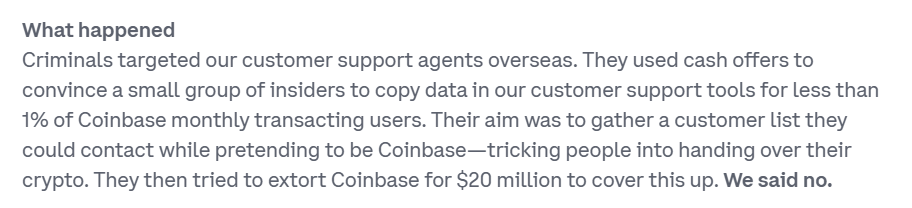
In a subsequent filing Coinbase estimated that the costs they suffered due to the breach are between $180 and $400 million.
The economics of this type of attack are insane. If the reported figures are accurate, a total of $500 000 in bribes resulted in at least $180 to $400 million in damages. The total value of the bribes amounted to less than 0.3 percent of the damage caused, and inflicting harm on Coinbase was not even the attackers’ main objective.
Discord Leak

In early October 2025, Discord announced that 70,000 government-issued IDs processed by the company had been leaked.
While not much is yet known about the nature of the attack, early reports suggest it may have involved an outsourced employee who accepted a bribe in exchange for photographing Discord user data:
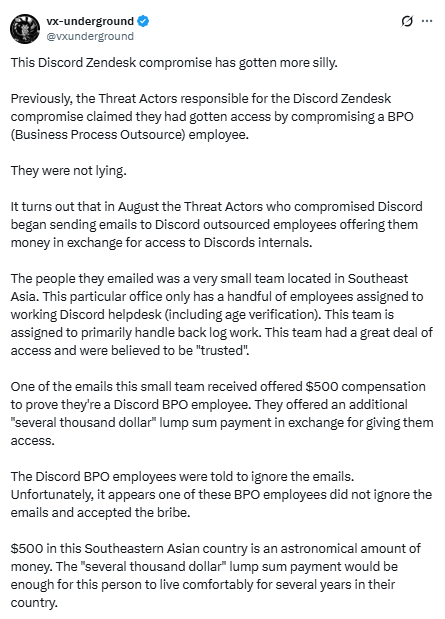
Reportedly, the hacker contacted a youtuber, which seems to further corrobarate the story of a $500 bribe to a BPO employee, with additonal payments promised after a successful hack.
The next part will be based on assumptions so take it with a grain of salt.
One company name that repeatedly appears in articles about the Discord breach is 5CA. The company has stated that it was not hacked, did not process government-issued IDs, and has attributed the incident to human error.
Several reports mention a BPO worker located in Southeast Asia. Looking at 5CA’s office locations, two are based in that region: Malaysia and the Philippines. Salary data for BPO roles in these countries ranges from about $200 per month on the low end in the Philippines to around $800 on the high end in Malaysia, based on figures from Glassdoor and Indeed.
While the total cost of this breach to Discord remains unknown, it is almost certain to exceed the $500 reportedly paid to bribe an outsourced employee, along with the promise of more to come.
Tesla (would be) Leak

Between July 15 and August 22, 2020, Igor Kriuchkov, affiliated with the REvil ransomware group, attempted to bribe a Tesla employee at the Gigafactory in Nevada to install malware on the company’s network. The employee was initially offered $500 000, which was later increased to $1 million.
The plan involved launching a DDoS attack after the malware was deployed to distract Tesla’s security team. During that time, REvil operators intended to encrypt and extract corporate data and then demand ransom.
What the REvil representative did not know was that the targeted employee had already alerted Tesla and was cooperating with law enforcement. This cooperation led to Kriuchkov’s arrest.
Although the identity of the Tesla employee remains unknown, part of the arrangement reportedly included sharing Tesla’s internal network details, suggesting the individual worked in IT. Based on publicly available data, IT roles at Tesla’s Nevada Gigafactory typically pay between $90 000 and $250 000 per year. In that context, the $1 million bribe represented roughly four to ten years’ worth of salary.
What Makes Bribery Possible
Outsourcing creates a ripe environment for bribery, especially when the outsourced roles combine low wages with high levels of access to sensitive systems or information.
Part of the reason is financial. Employees earning low wages are more likely to accept bribes1. This means that the barrier to accessing an organization’s sensitive data (or that of its clients ) can be as low as $200, as seen in the Coinbase case.
Another factor is perceived unfairness. Many outsourced employees ask themselves, “Why am I being paid significantly less than my Western counterpart?” While it is normal for global organizations to adjust salaries based on local cost of living, employees who view their compensation as unfair or inadequate are significantly more vulnerable to bribery.2
There is also the issue of belonging. Outsourced employees may not feel as valued, included, or connected to the organization as in-house staff3. This sense of detachment can make them feel like outsiders rather than integral members of the team.
Geography compounds these risks. Common outsourcing hubs such as India and Southeast Asia are often located far from the organization’s headquarters, where leadership and oversight reside. This physical and managerial distance can create oversight gaps, even for employees working in official overseas offices.
Finally, the scale and nature of the task also influence bribery risk. In the Coinbase case, BPO employees were bribed to take photos of their screens which is a low-effort, low-risk act. By contrast, in the Tesla incident, the employee was asked to manually install malware at a facility where they worked, a much higher-risk and higher-skill task.
This weaker organizational identity, combined with oversight gaps and strong economic incentives, makes outsourced employees significantly more likely to accept an offer that compromises security – whether that means sharing access credentials, leaking data, or assisting in a breach.
What to Do About It
From a security monitoring perspective, I see three main insider threat scenarios related to bribery:
- Employees exfiltrating data themselves
- Employees sharing credentials with threat actors
- Employees installing malware on systems they can access
All of these can be detected to varying degrees of success. The real challenge lies in attributing such actions to bribery rather than digital compromise. From the outside, the behavior of an insider who installs malware intentionally look almost identical to that of an employee whose account has been compromised.
Still, several controls come to mind when thinking about how to mitigate bribery risk.
Establish a Whistleblower Channel
Is there a trusted way for employees to report suspicious behavior, for example, overhearing a suspicious conversation, seeing someone take photos of their screen, or witnessing a bribery attempt?
If not, consider setting one up that:
- Ensures employee anonymity and protection from retaliation
- Bypasses local management (since they might be part of the issue)
- Includes regular training on how to use it; reinforce awareness with physical reminders in offices
Use Data Loss Prevention (DLP)
Understanding what happens to your sensitive data is essential to spotting exfiltration attempts, whether through removable drives or less common channels.
Modern DLP tools also help identify where data resides and who has access to it. This visibility improves control over data handling and reduces opportunities for unauthorized exfiltration.
Apply Anomaly Detection
Anomaly-based detection can be inconsistent, but it remains valuable when tuned properly. Look for unusual behaviors such as access outside business hours, logins from new locations or devices, or sudden changes in data-handling patterns.
While these signals can be noisy, when correlated with other indicators, they can point toward insider activity or a potential bribery case.
Monitor for Audit Trail Deletions
Attempts to delete audit trails are among the loudest actions an attacker or insider can take, assuming monitoring is in place. Most attempts to tamper with logs reveal suspicious activity that often extends beyond bribery itself. This area deserves special focus if you are concerned about insider manipulation or cover-ups.
Establish Granular Access Control
Granular access control reduces the risk of misuse if credentials are shared with threat actors.
Implement just-in-time access for privileged roles, so elevated permissions are only active when needed. For outsourced IT staff, add an approval step to ensure each activation aligns with a legitimate change window or support request.
SecOps vs Bribery
Traditional security operations are built to stop technical compromise like malware infections, phishing campaigns, credential theft. Bribery is a different kind of threat. It blends human motivation, economic pressure, and organizational blind spots.
There are things you can do – some easier, like monitoring for audit trail deletions or establishing whistleblower channels, and others more complex, such as building an effective DLP program, tuning anomaly detection properly, or implementing granular and resilient access controls.d
I usually avoid talking about culture, but the data and common sense both point in the same direction: employees who feel like they are genuinely part of the organization are far less likely to become the human link in a bribery attempt. Investing in that sense of inclusion and fairness may not show up in your SIEM, but it can close one of the more dangerous gaps in modern security operations.
- In a controlled experiment conducted by Roel van Veldhuizen and then published in a Discussion Paper, low-wage participants accepted bribes ~91% of the time, compared with ~38% for higher-wage participants. ↩︎
- Abbink, K. (2002). Fair salaries and the moral costs of corruption. Nottingham University, Centre for Decision Research and Experimental Economics (CeDEx). https://www.nottingham.ac.uk/cedex/documents/papers/2002-05.pdf ↩︎
- Yang, J. F., Chen, S., Zhang, H., & Zhang, Y. (2023). Are “outsiders” in? Exploring the impact of outsourced employees on perceived insider status. Frontiers in Psychology, 14, 1236309. https://doi.org/10.3389/fpsyg.2023.1236309 ↩︎



Leave a comment